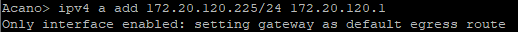
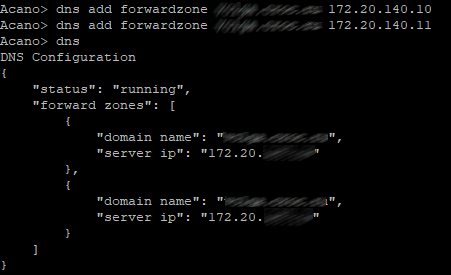
Part 2 explains call settings, Incoming and Outbound calls configuration, spaces and CUCM certificates
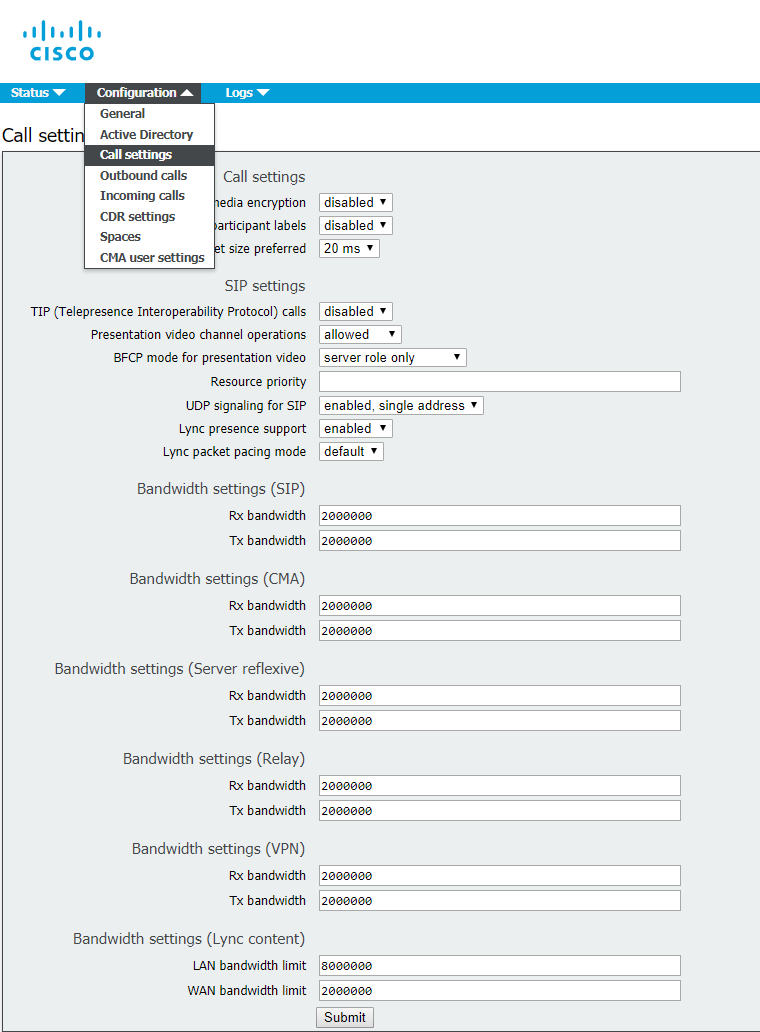
Basic Call Settings Configuration
Proceed to Configuration > Call settings and set the values as given below:
Incoming Call Handling Configuration
Proceed to Configuration > Incoming calls and set the values as specified below:
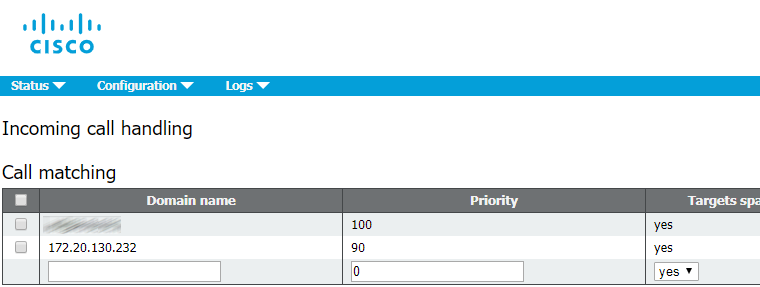
This configuration determines the way of incoming SIP calls handling on CMS. Any call routed to CMS will have a verified alias. The rules in call matching table determine where CMS will look for potential matches. Each rule can be set to match any combination of users, IVR or MicrosoftSkype / Lync. To handle incoming calls, Cisco Meeting Server tries to match the value after "@" sign with the values in “domain name” column.
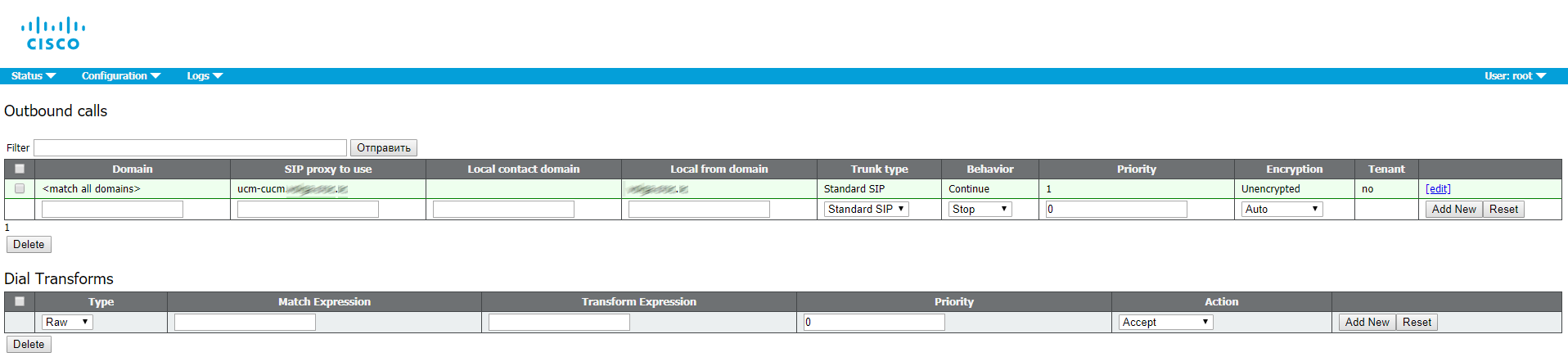
Outbound Call Handling Configuration
Proceed to Configuration > Outbound calls.
Domain name: leave empty (to match all domains)
SIP Proxy to use: enter your CUCM FQDN (IP address is admissible, but FQDN is recommended)
Local contact domain: leave empty, it is only needed for Skype for Business SIP Trunk configuration.
Local from domain: enter Cisco Meeting Server SIP domain (e.g. cms.example.com)
Trunk type: Standard SIP
Behavior: Continue
Priority: 1
Encryption: Auto or Unencrypted
Click Add New to save the changes.
Space Creation
Create a space where the users will be stored.
Proceed to Configuration > Spaces
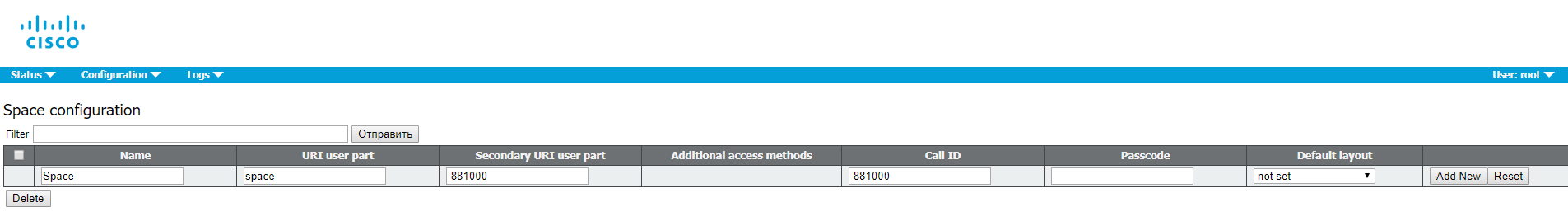
The Secondary URI should be a E.164 value compatible with your dial plan that will be routed to CMS. The CallID can be any number that is not used yet. In this example we use the same value as for Secondary URI.
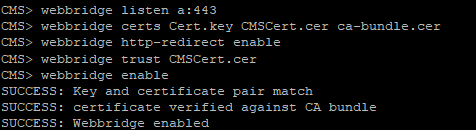
Configure Web Bridge for Call Bridge
To allow guest access to Web Bridge, configure Call Bridge to set Web Bridge address.
Proceed to Configuration > General
Configure a HTTPS CMS URL address for a guest account. For example:
meetingserver.example.com
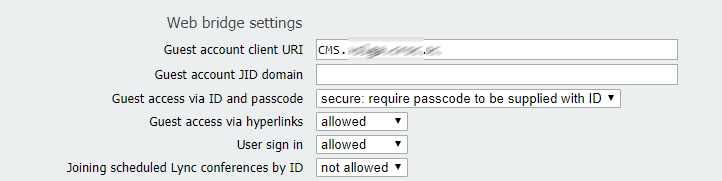
Fill External Access field if you want to add Cisco Expressway web proxy. This address will be used in invites for external users.
CUCM Certificates
Perform the requests for Tomcat (CUCM web server) and CallManager services.
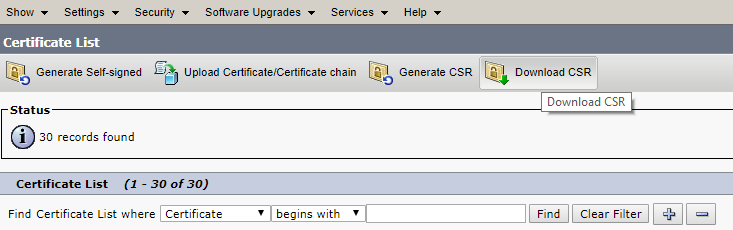
Proceed to Cisco Unified OS Administration > Security-Certificate Management and click Generate CSR.
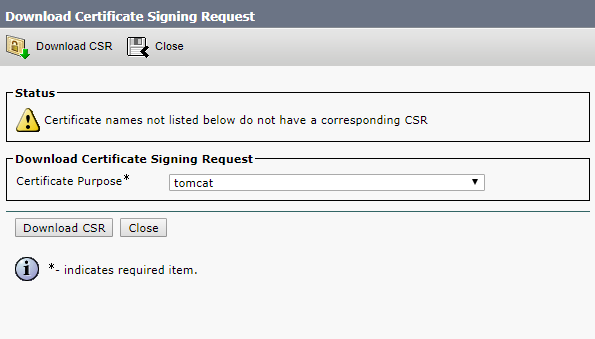
First, select Tomcat in the Certificate Purpose field, so you won’t get errors in your browser.
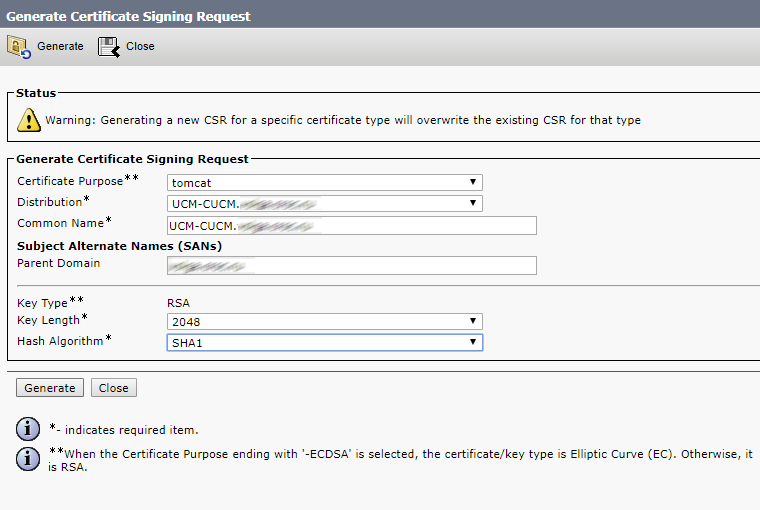
Click Generate.
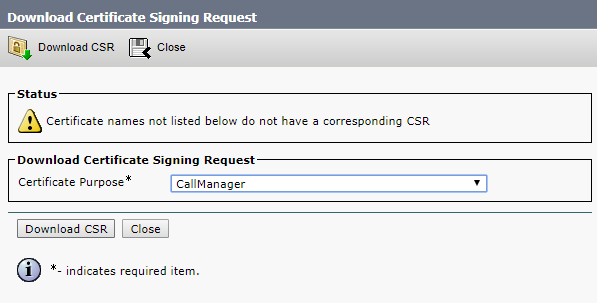
Then select CallManager, so CMS and CUCM will check each other’s certificates for Conference Bridge registration.
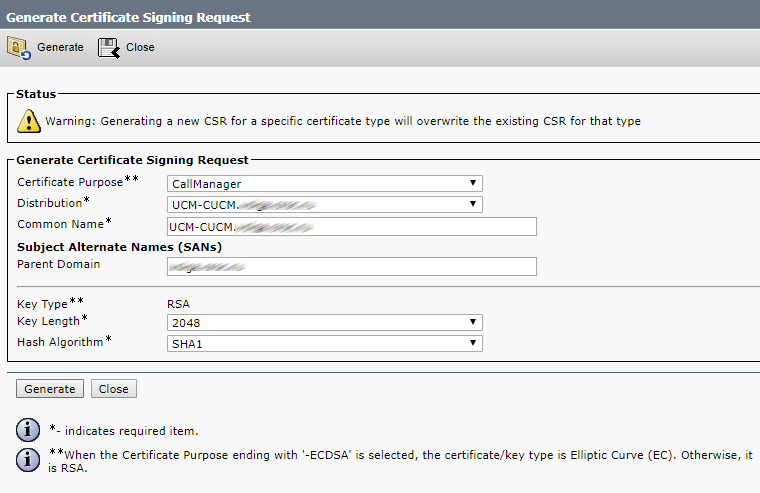
Click Generate.
Now download the certificate signing request files for CA.
Upload root and intermediate certificates for Tomcat-trust and CallManager-trust, either one by one (root certificate first) or as a single file (as described above).
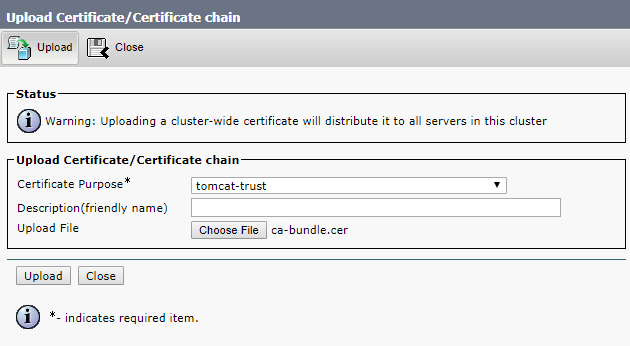
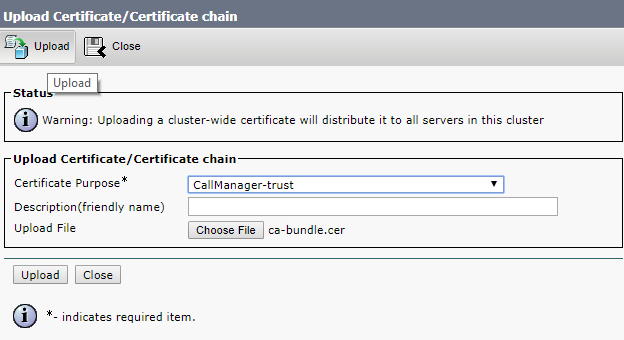
Click Upload.
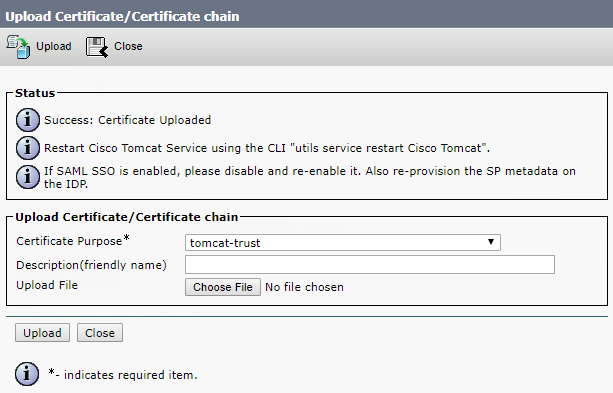
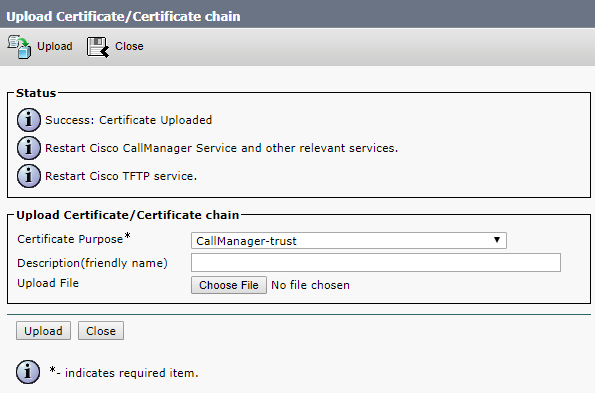
Upload the CA certificate files formed upon your request.
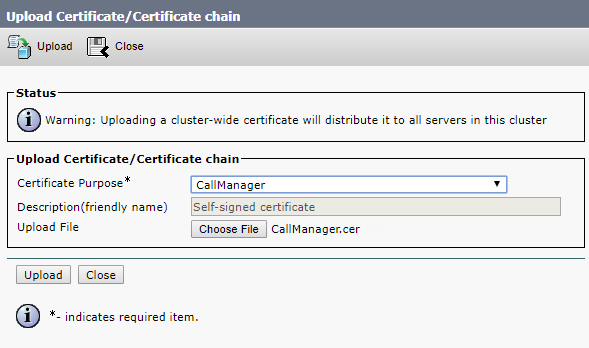
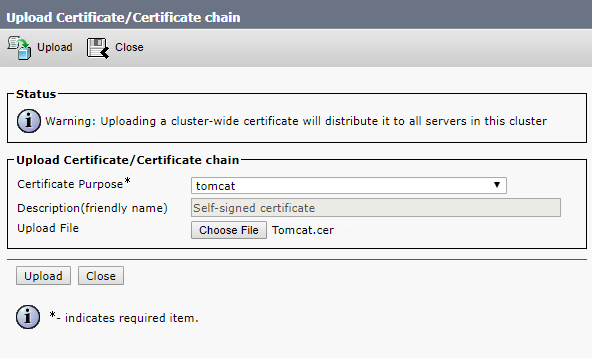
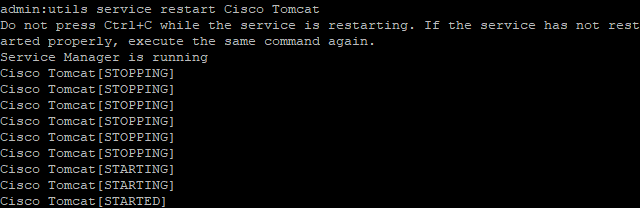
Now restart Cisco Tomcat, Cisco CallManager and Cisco TFTP services.
Restart Cisco Tomcat from the command line.
The other ones can be restarted from web interface.
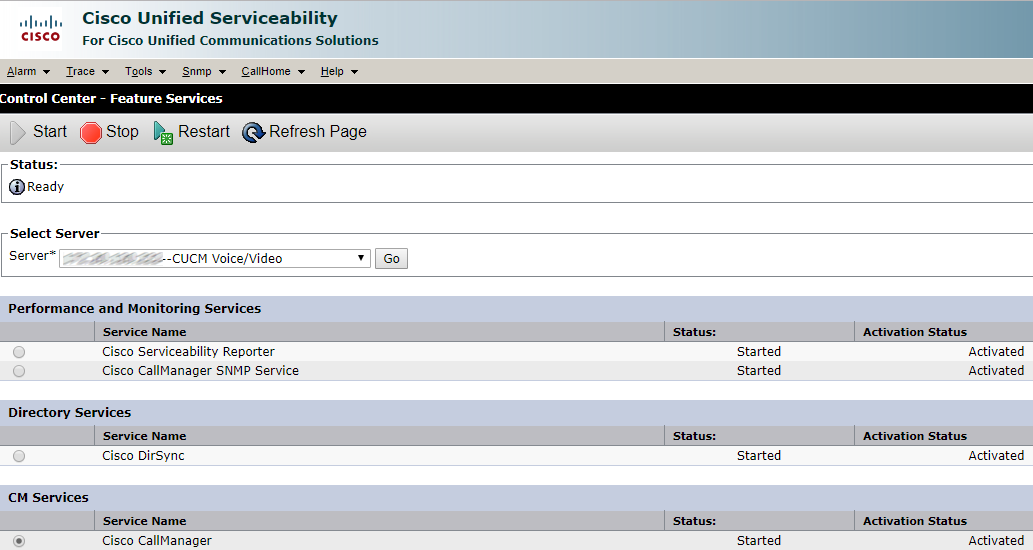
Click Restart and wait for the services to be restarted.
Read also:
- Part 1 - Integration of Cisco Meeting Server with CUCM 11
- Part 2 - Integration of Cisco Meeting Server with CUCM 11
- Part 3 - Integration of Cisco Meeting Server with CUCM 11
This article is a translation of a guide originally created by S. Dubinin, Telecommunications Specialist - https://habr.com/ru/post/433528/