
What are you missing in Cisco Meeting Server?

Integration of Cisco Meeting Server with CUCM 11 – PART 3

The last part is about SIP trunking, сonference bridge, route patterns and users.
SIP trunk security profile
Now create a SIP trunk security profile.
If the calls won’t be encrypted, select the values specified below. Enter Call Bridge certificate CN (your CMS server FQDN).
Check Accept Replaces Header if you are going to use conference call bridges.
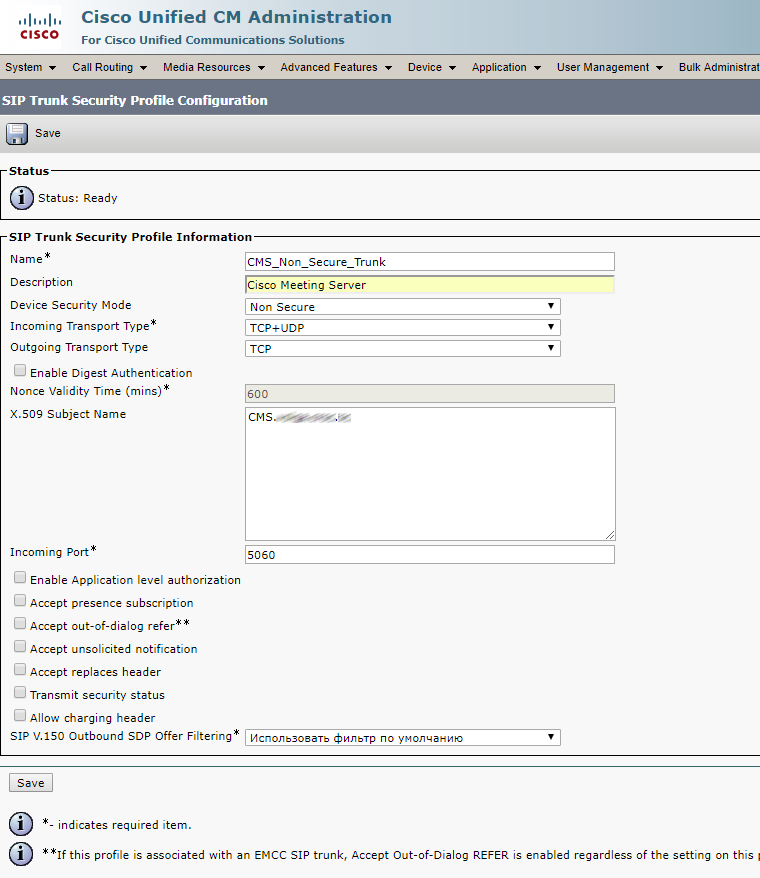
Conference Bridge
Create a Conference Bridge as described below. Enter username and password of the user with appadmin role (we have created this user in the very beginning).
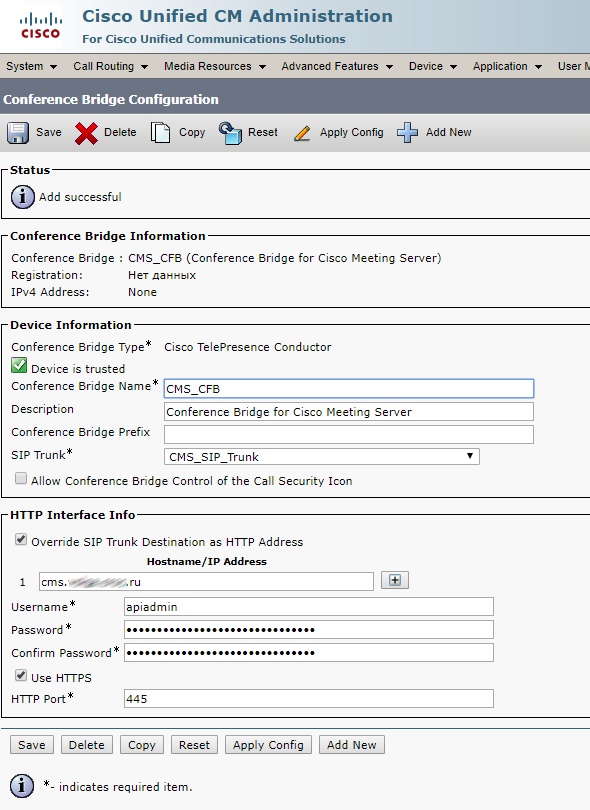
Create a Media Resource Group and add your Conference Bridge there.
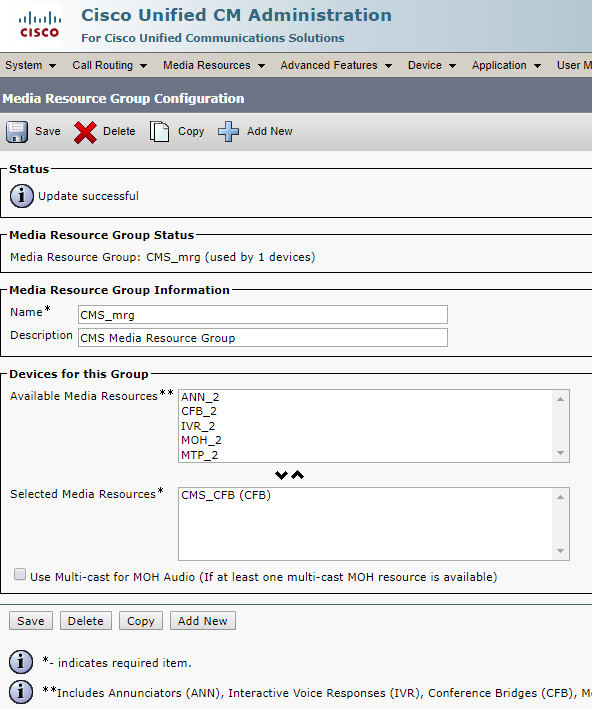
Create Media Resource Group List and add your Media Resource Group there.
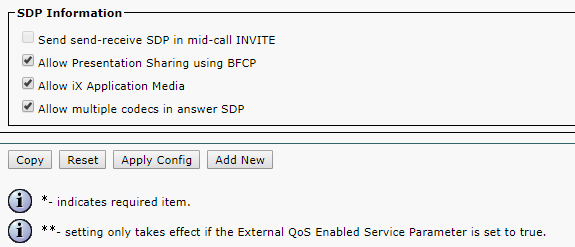
Proceed to Standard SIP Profile For TelePresence Conferencing and make sure that Allow iX Application Media, Use Fully Qualified Domain Name in SIP Requests, and Allow Presentation Sharing use BFCP options are checked.
SIP Trunk
Now create a SIP Trunk to CMS server.
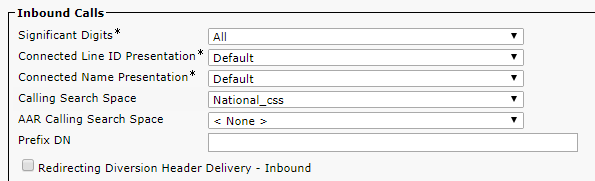
You should set the correct Calling Search Space, so calls will be successful. Otherwise, CMS won’t be able to find the required phone number. Both the device and the phone number have to be added to the Calling Search Space.
Media Resource Group List — select the one you have created.
SRTP Allowed flag allows encrypted calls. You can disable it.
SIP Information > Destination address — enter your CMS FQDN or IP address.
SIP Information > Destination Port — standard SIP port is 5060, 5061 is for encrypted calls.
SIP Trunk Security Profile — select the one you have created.
SIP Profile — select Standard SIP Profile For TelePresence Conferencing
Normalization Script — don’t set. It is only needed for encrypted calls. Set cisco-telepresence-conductor-interop if you are using encryption.
Pay attention to the green marked parameters. You should gain an understanding of Calling Search Spaces to fill them correctly.
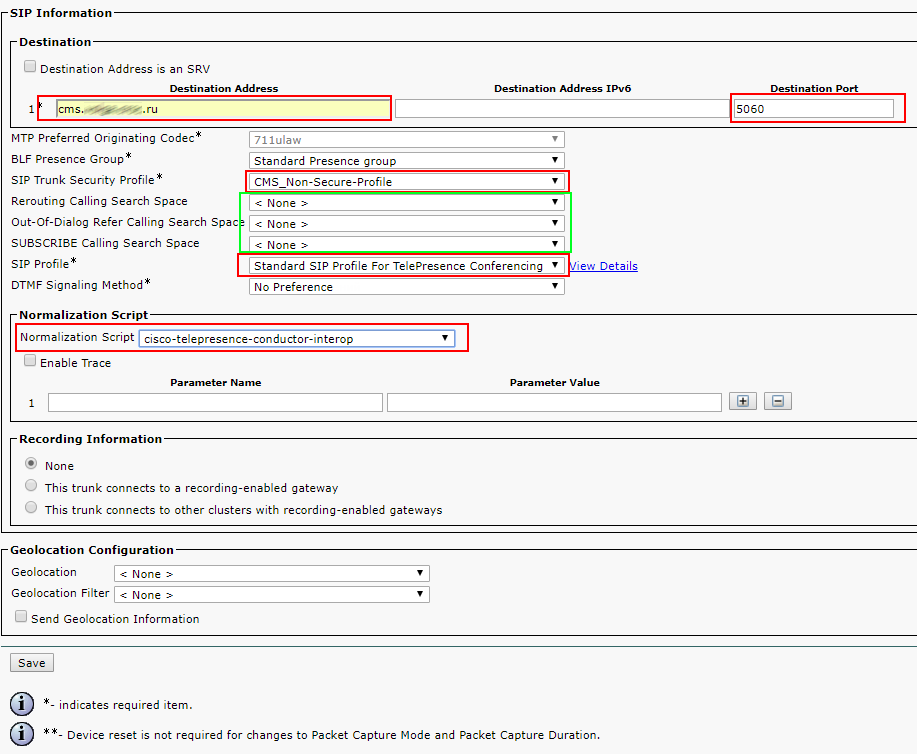
Leave other fields with default values.
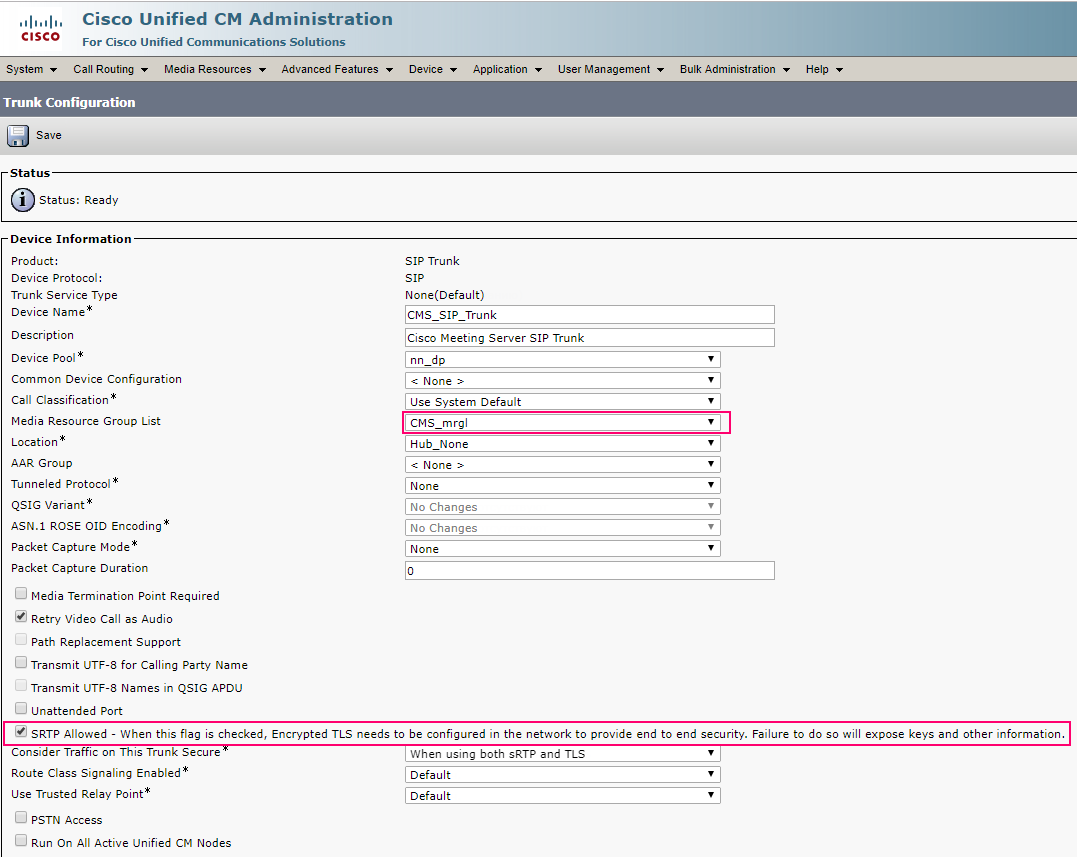
SIP Route Pattern
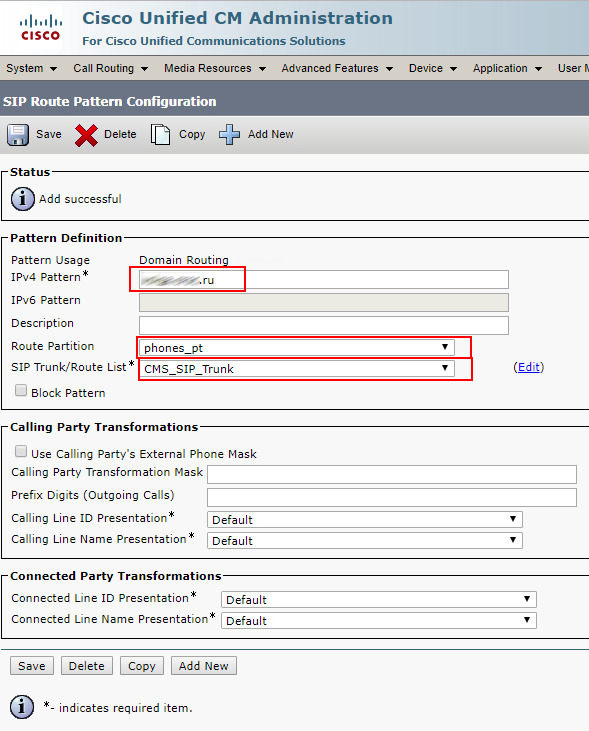
Create a SIP Route Pattern for calls to SIP addresses like smith.j@example.com
Check CMS and CUCM:
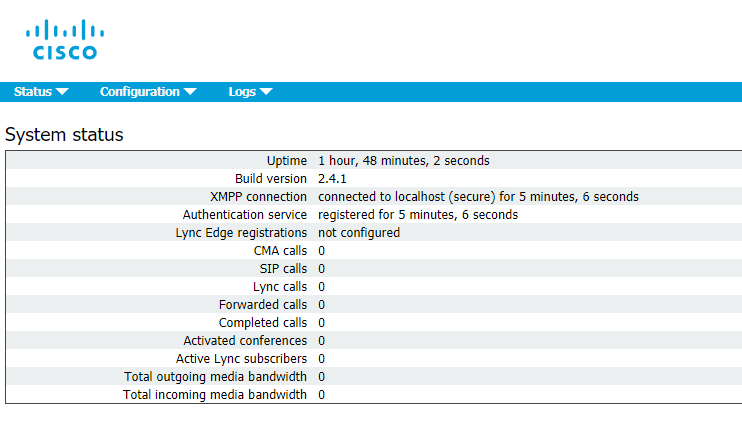
The trunk is up.
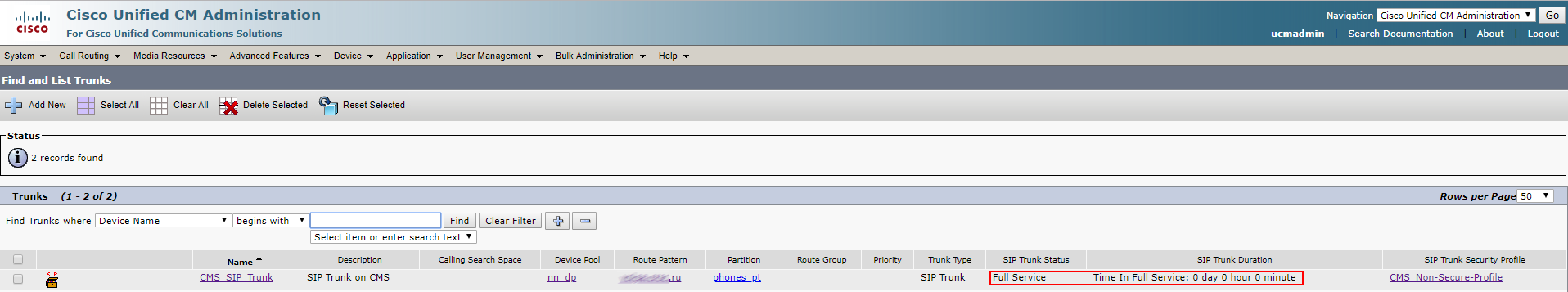
However, the Conference Bridge is down due to the difference in TLS versions on CUCM and CMS. This issue can be solved by TLS 1.0 installation on CMS:
tls webadmin min-tls-version 1.0
webadmin restart
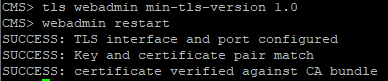
Check the Conference Bridge:

Our configuration is being performed on trunks without Media Termination Point (MTP).
Disable MTP if it won’t affect your services.
Disbling MTP can affect your services if your phones use SCCP protocol and you have to send DTMS to CMS.
If this is true for your services, you may have to increase MTP capacity on CUCM depending on the number of simultaneous calls.
Importing Active Directory Users
Now import the users from Active Directory.
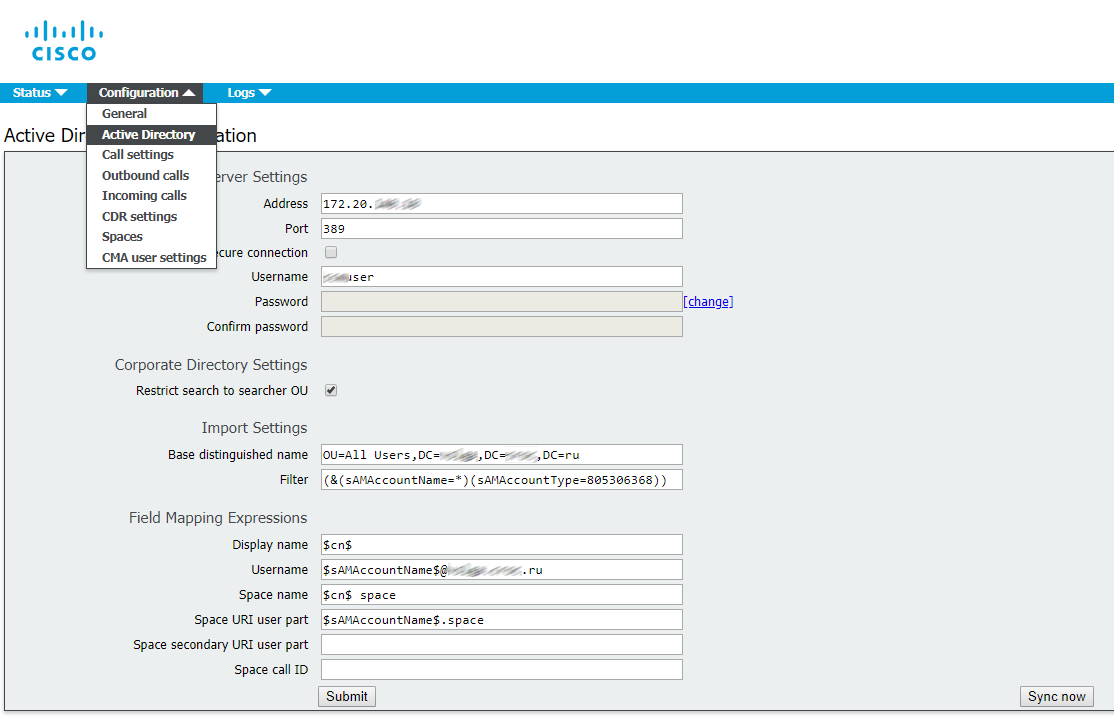
Proceed to Configuration -> Active Directory, fill out the fields (see the figure below).
Filter is a very important field. You can enter your own filter or use the filter shown on the picture.
Look through the logs.
Everything is right.
Proceed to Status -> Users to make sure that all users have been imported.
Availability check
We got to the best part.
To perform a call, access the web interface: cms.example.com
Enter an Active Directory user login and password to log in.

Now let’s check a video call from an IP Phone (we are using Cisco E20) to our user account.
I have web and desktop Cisco Meeting clients running, and both are calling.
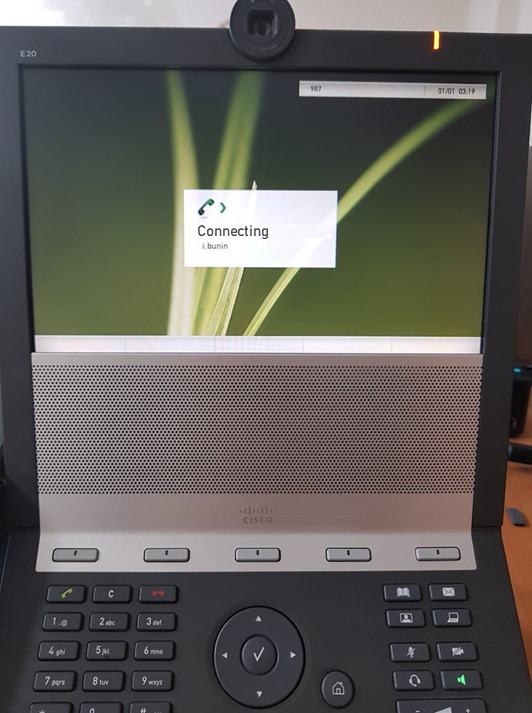
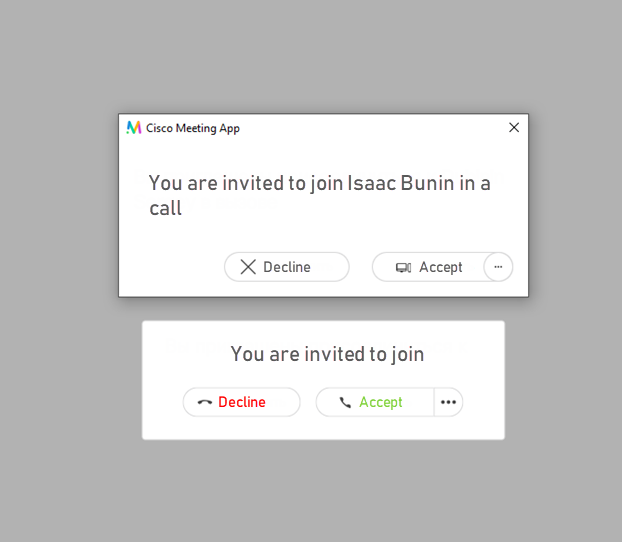

You can also test the video call from your user account to IP Phone. In our case, the video call was successful in both directions.
Encrypted calls can bring in some complications, but that’s a story for another day.
See also:
- www.cisco.com/c/dam/en/us/td/docs/conferencing/ciscoMeetingServer/Deployment_Guide/Version-2-3/Cisco-Meeting-Server-Single-Server-Simplified-Setup-Guide.pdf
- www.cisco.com/c/dam/en/us/td/docs/conferencing/ciscoMeetingServer/Deployment_Guide/Version-2-5/Cisco-Meeting-Server-2-4-and-later-Deployments-with-CUCM.pdf
- cisco.com/c/dam/en/us/td/docs/conferencing/ciscoMeetingServer/Reference_Guides/Version-2-4/Cisco-Meeting-Server-MMP-Command-Reference-2-4.pdf
Read also:
- Part 1 - Integration of Cisco Meeting Server with CUCM 11
- Part 2 - Integration of Cisco Meeting Server with CUCM 11
- Part 3 - Integration of Cisco Meeting Server with CUCM 11
This article is a translation of a guide originally created by S. Dubinin, Telecommunications Specialist - https://habr.com/ru/post/433528/
